File Processing
Nodes used to process files, increase their value, or remove threats.
File Processing forms the core economic loop of the system, involving the continuous downloading, cleaning, validating, enhancing, and uploading of various file types. This process converts network data into monetary gains and research points.
I. Core File Flow and Download
The entire process generally flows from left-to-right, starting with network access and ending with collection.
- Network Downloader: The process begins by connecting the download speed output to a specific file downloader (e.g., Text Downloader).
- File Types: Files are downloaded and processed sequentially as capabilities are unlocked:
- Text
- Image
- Sound
- Video
Files downloaded initially are "raw" and have not undergone cleaning, validation, or modification.
II. Processing Power and Speed
Processing nodes utilize Clock Speed to execute tasks like scanning, checking integrity, and enhancing.
- CPU/Processor Cell: These nodes provide the necessary processing power. Clock Speed, which represents the processing speed, can be upgraded using cash.
- Cores: Adding multiple cores allows dedicated processing power to be supplied to specific processing lines (e.g., dedicating a core to virus scanning).
- Synchronizer Nodes (Parallelism): These nodes allow CPU and GPU cores to work synchronously, improving efficiency.
III. File Validation and Cleaning Pipeline
Downloaded files often carry modifiers that must be addressed to maximize value. Downloaded files have a 50% chance of being infected (virus), which reduces their value by four times.
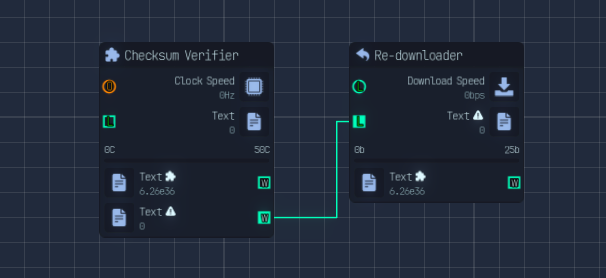
1. Checksum Verification
The Checksum Verifier (unlocked via research) verifies the integrity of the incoming files.
- If files are validated, they are worth four times more.
- Processing power must be supplied to the Checksum Verifier.
2. Virus Scanning and Removal
The virus control system involves multiple nodes dedicated to identifying and fixing infections:
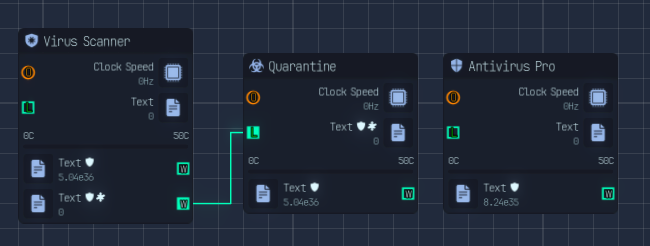
- Virus Scanner: Scans files using clock speed, adding a "scanned" modifier and increasing the value by four times.
- Quarantine (Antivirus Plus): Unlocked via upgrade. This node removes the infected modifier from the files.
- Antivirus Pro: Unlocks the ability to scan and remove viruses from files, also increasing their value by four.
3. Redownloading and Repair
The Redownloader (unlocked for 3K Science) fixes corrupted files and increases their value. This node requires an independent download line connection to function.
4. Organization Nodes
Processing lines utilize specialized nodes for flow management:
- Folders: Used to consolidate "good" or cleaned files before they proceed to enhancement or uploading.
- Repository: Functions similarly to a folder, storing resources of the same type and combining them into a single output.
IV. Value Optimization and Enhancement
Once files are validated, they are enhanced to maximize revenue.
1. Enhancers
The Enhancer node enhances the quality of a file using clock speed, adding the "enhanced" modifier and increasing its size and quality by two.
- Enhancing files requires clock speed.
- Multiple enhancers can be stacked in sequence to maximize value (e.g., using three enhancers).
2. Compression
Compression reduces the file size.
- Incompressor (Application Point upgrade): A highly efficient tool that enhances and compresses files simultaneously, increasing value by 2x and reducing size by 2x. This node is designed to potentially replace separate Enhancer and Compressor nodes.
3. Data Refinement
The Data Refiner (unlocked via research) refines files specifically for an increased research value.
V. Advanced Systems and Upload
1. Artificial Intelligence (AI) Integration
Once AI is unlocked, the file validation pipeline can be significantly simplified:
- The AI Trainer/Generator system can utilize raw files (no prior processing).
- AI automatically strips all viruses out and performs a checksum, adding the AI tag to the files.
- AI generation can replace the need for Checksum, Redownloader, Quarantine, and Virus Scanner nodes.
2. Output and Collection
- Uploader: Processed files are routed to an Uploader node, which connects to the network to generate money.
- Allocator: Used to divide file output into specific ratios, directing some output for financial upload and others for specialized requests (like research or tokens).
- Premium Upgrades: Purchased using money, the "Premium" upgrade status increases the value of specific file types (Text, Image, Sound, Video) by 100%.
- Auto Collector: Purchased with 40 Tokens, this node automatically collects the money generated from the uploaded files, removing the need for manual clicking.
